SentryBay Armoured Client for Citrix NetScaler Configuration Guide v1.0
NetScaler / SentryBay Armoured Client for Citrix Configuration
This guide is an example of how the Armoured Client’s browser user-agent string can be detected and routed accordingly. There are many methods of doing this with NetScaler by using either of the following features:
- NetScaler Gateway Session Policy
- Content Switch
- Rewrite
- Responder
This guide uses NetScaler Gateway Session Policy as is the easiest and works with all editions of NetScaler and NS Gateway, plus allows the configuration of the end user instructions to easily be controlled and applied in a separate Storefront Store.
If the user successfully authenticates the Session Policy will try to detect the user agent string set in the SentryBay Armoured Client and if it does will route to the normal Storefront Store.
A second Storefront store is configured whereby only web links to internal sites will be present, where the user will find instructions on where to download and install the Armoured Client. It would also be possible to publish un-restricted applications to this store in this scenario where the Armoured Client is not being used, if desirable.
Figure 1 below shows the concept, with the relevant Polices and Profiles as detailed in the remaining sections of this document.
Disclaimer:
The User-Agent string can easily be spoofed so is not a 100% safe security control, but does allow the organisation to easily distribute and run a basic enforcement policy. However, the user must authenticate in the normal way, using existing Access Controls that are configured and enforced on the Citrix NetScaler today by the individual organisation.
A future document will be provided on how to set up client based certificates with the NetScaler and Armoured Client, to further prove authenticity.
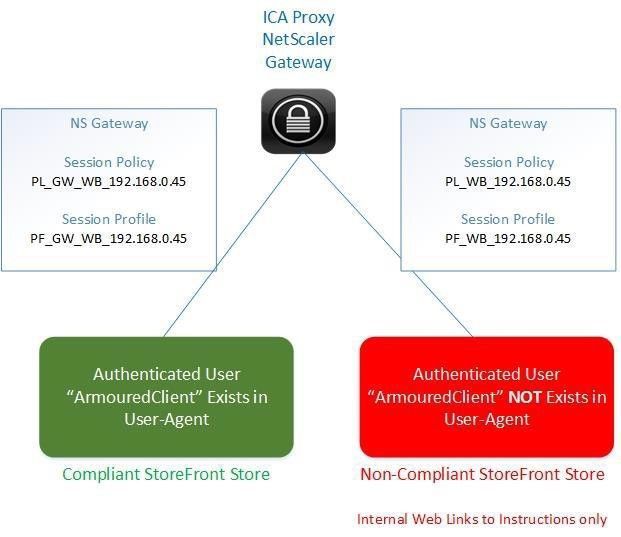
Figure 1 – NS Gateway Session Policies with 2 StoreFront stores
Armoured Client Detection Policy & Profile
Create and configure a Session Policy and Profile for Users who:
- Successfully Authenticated
- SentryBay Armoured Client detected
This will be configured to point at the compliant StoreFront store.
Trusted Session Profile
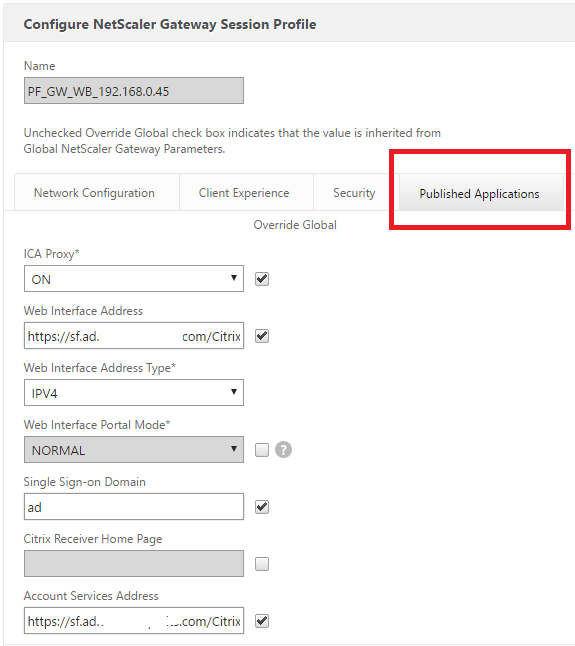
add vpn sessionAction PF_GW_WB_192.168.0.45 -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -homePage “https://sf1.ad.XXXXX.com/citrix/uatweb/” -icaProxy ON -wihome “https://sf.ad.XXXXX.com/Citrix/uatweb/” -ClientChoices OFF -ntDomain ad -clientlessVpnMode OFF -storefronturl https://sf.ad.XXXXX.com/Citrix/uatWeb/
Trusted – Session Policy
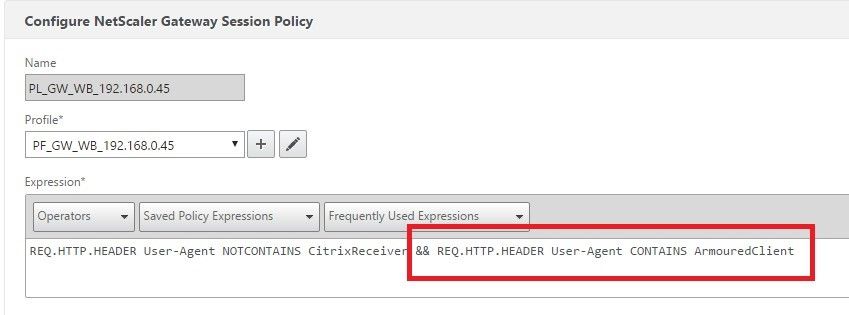
add vpn sessionPolicy PL_WB_192.168.0.45 “REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver” PF_WB_192.168.0.45
Note the spelling of “ArmouredClient” as has been hard coded. In future releases this may change and also we plan to allow this to be a ‘per customer’ setting in the individual build.
Non-Armoured Client Detection Policy & Profile
Create and configure a Session Policy and Profile for Users who:
- Successfully Authenticated
- SentryBay Armoured Client is NOT detected
The standard Web Session Policy and Profile will catch all other Web Client requests where the user- agent string does NOT contain “ArmouredClient” and be configured to point to a different Storefront store which will have only published link/s to internal web page/s instructing the user how to download and install the Armoured Client.
Note: You will need to create a StoreFront store for Untrusted Sessions which is beyond the scope of this document, but straightforward to do.
Untrusted – Session Policy
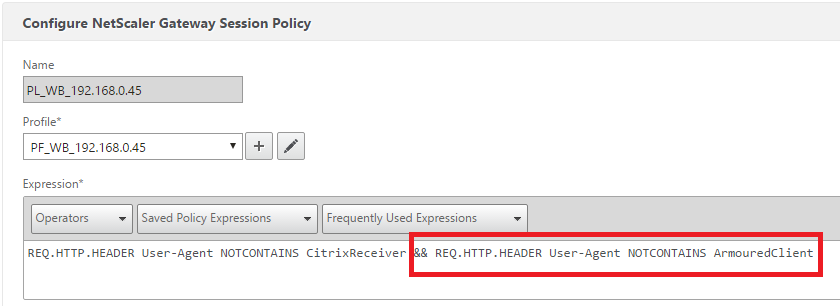
add vpn sessionAction PF_WB_192.168.0.45 -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -homePage “http://sf1.ad.XXXXX.com/citrix/storeweb/” -icaProxy ON -wihome “https://sf.ad.XXXXX.com/Citrix/storeweb/” -ClientChoices OFF -ntDomain ad -clientlessVpnMode OFF -storefronturl https://sf.ad.XXXXX.com/Citrix/storeWeb/
Set the Web Interface Address in the Session Profile to be the Untrusted Store URL / Name that you have configured in StoreFront.
Untrusted – Session Profile
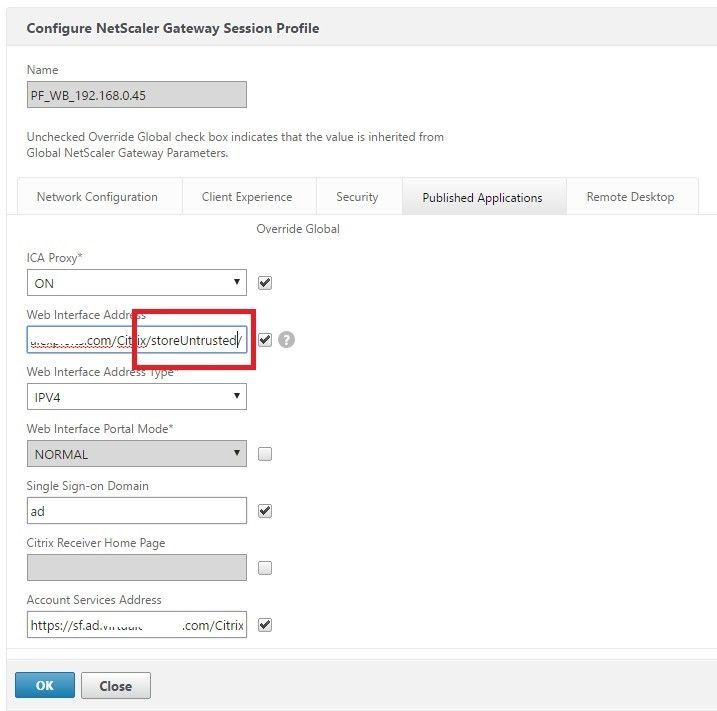
add vpn sessionPolicy PL_WB_192.168.0.45 “REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver” PF_WB_192.168.0.45
Policy Binding to Gateway
Both Session Policies must be bound to the Gateway Virtual Server.
The first policy created which catches the “ArmouredClient” string if present should be bound with a lower priority number (so that it gets processed first).
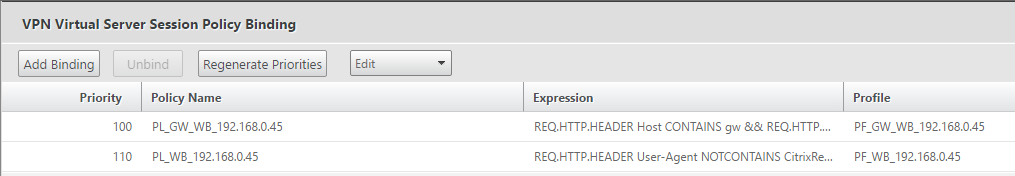
bind vpn vserver _XD_ag1 -policy PL_WB_192.168.0.45 -priority 110
bind vpn vserver _XD_ag1 -policy PL_WB_192.168.0.45 -priority 110
Testing / Expected User Experience
Finally test by:
- Logging on to the Gateway using a normal browser – which once authenticated should direct you to the Non-Compliant StoreFront Store.
- Logging on to the Gateway using The SentryBay Armoured Client – which once authenticated should direct you to the Compliant StoreFront Store.
If you require further information please do not hesitate to contact SCG via email on info@stadiacg.co.uk or via telephone on +44 (0) 20 7 0399 266 .
The post SentryBay Armoured Client for Citrix NetScaler Configuration Guide v1.0 appeared first on SCG - Stadia Consulting Group.



CONTACT US
+44 (0) 207 0399 266
info@stadiacg.co.uk
Stadia Consulting Group
8 Prykes Drive, Chelmsford, Essex CM1 1TP
USEFUL LINKS
All Rights Reserved | Stadia Consulting Group Ltd


